Human rights activists in Morocco and the Western Sahara region are being targeted by a new threat actor identified as Starry Addax, which employs sophisticated phishing attacks to compromise their security. Cisco Talos, which is tracking this activity, reports that Starry Addax specifically targets activists associated with the Sahrawi Arab Democratic Republic (SADR). The group's infrastructure is designed to deceive both Android and Windows users, using domains such as ondroid[.]site and ondroid[.]store.
For Android users, Starry Addax tricks victims into installing fake apps, while for Windows users, they create counterfeit websites that imitate popular social media login pages to harvest credentials. This dual-pronged approach increases the likelihood of successfully compromising targets across different platforms. Due to the ongoing nature of the investigation, Talos has not publicly disclosed which specific websites are being used in these credential harvesting attacks.
Starry Addax's campaign highlights the persistent and evolving threats faced by human rights activists in politically sensitive regions. By targeting those involved with the SADR, the group underscores the geopolitical dimensions of cyber threats. The sophistication of their methods, involving both mobile and desktop platforms, reflects a strategic effort to maximize the reach and impact of their malicious activities.

Human rights activists in Morocco and the Western Sahara region are being targeted by a sophisticated threat actor known as Starry Addax. This group, tracked by Cisco Talos, has been active since January 2024 and specifically targets activists associated with the Sahrawi Arab Democratic Republic (SADR). Starry Addax employs advanced phishing techniques to compromise both Android and Windows users. They establish their own infrastructure, using domains like ondroid[.]site and ondroid[.]store, to host credential harvesting pages designed to look like legitimate login pages for popular media and email services.
The group sends spear-phishing emails to their targets, often urging recipients to install what appears to be the Sahara Press Service's mobile app or other relevant decoy applications related to the region. Depending on the target's operating system, the phishing emails either deliver a malicious APK that impersonates the Sahara Press Service for Android users or redirect Windows users to fake social media login pages to steal their credentials. This dual strategy enhances the group's ability to deceive and compromise a broad range of targets across different platforms.
By creating fake login pages that mimic widely used services, Starry Addax aims to harvest sensitive information such as login credentials, which can be used for further exploitation. The group's ability to craft convincing spear-phishing emails and establish their own hosting infrastructure underscores the level of sophistication and resources behind their operations. Due to the ongoing investigation, specific details about the targeted websites have not been disclosed by Talos.
The campaign by Starry Addax highlights the ongoing and evolving threats faced by human rights activists in politically sensitive areas. Their targeted approach, combined with the use of both mobile and desktop platforms, indicates a strategic effort to maximize the reach and impact of their malicious activities. This poses a significant risk to activists in the region, as the stolen credentials could lead to further surveillance, harassment, or other forms of cyber exploitation.

A novel Android malware known as FlexStarling has emerged, demonstrating remarkable versatility and capabilities for delivering additional malware components and extracting sensitive information from compromised devices. Upon installation, FlexStarling prompts the victim to grant it extensive permissions, enabling the malware to execute various malicious actions. Notably, it fetches commands from a Firebase-based command-and-control (C2) server, indicating the threat actor's intention to operate covertly.
According to Talos, campaigns targeting high-value individuals, like this one, typically aim to remain undetected on the device for prolonged periods. The malware and its associated infrastructure appear to be custom-made for this specific campaign, suggesting a strong emphasis on stealth and clandestine operations.
This development coincides with the emergence of Oxycorat, a new commercial Android remote access trojan (RAT) available for purchase. Oxycorat boasts diverse information-gathering capabilities, adding to the arsenal of threats targeting Android devices. These developments underscore the evolving landscape of Android malware and the growing sophistication of threat actors, highlighting the need for robust cybersecurity measures to protect against such threats.
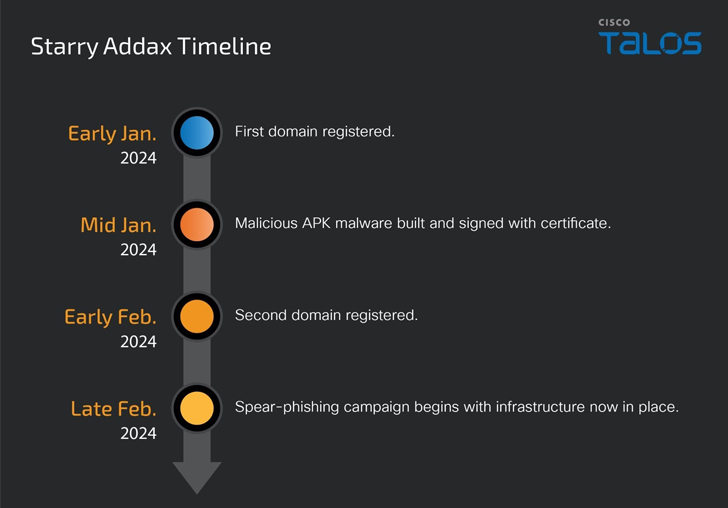
The latest findings reveal an intriguing development: Starry Addax has opted to construct its own arsenal of tools and infrastructure rather than relying on off-the-shelf malware or commercially available spyware to target human rights activists.
According to Talos, while the attacks are still in their early stages operationally, Starry Addax has invested considerable effort in developing its supporting infrastructure and malware, FlexStarling. This indicates that the group considers FlexStarling to be sufficiently mature to initiate targeted campaigns against human rights activists in North Africa.
The timeline of events, which includes the establishment of drop points, command-and-control servers, and the development of malware since early January 2024, suggests that Starry Addax is rapidly expanding its infrastructure to target high-value individuals. As a result, the group is expected to continue gaining momentum in its efforts to compromise the security and privacy of its targets.
Categories: Cyber Security, Computer Tags: #romania, #asia







